Imagine having an open architecture secure credential with custom keys that can only be used within your enterprise. As your encryption key custodian, we design the custom key sets and you have 100% full ownership!

After understanding your requirements, K&A’s engineering team will create unique secure crypto key sets for each data application on the new credential, ensuring no other installation worldwide uses these unique keys.
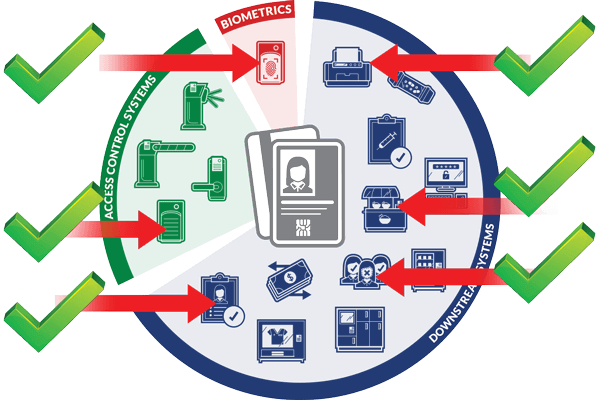
Personalized data, such as employee IDs, can be embedded in RFID chips during card production. This enables secure credentials for enterprise-wide access control and tasks like secure printing, dining, vending, and biometrics.

K&A will model the new technology in a test lab, putting all the elements together in a sandbox environment, making sure cards would work seamlessly with the newly programmed readers throughout the migration.
Cards with LIMITLESS APPLICATIONS —
each with its own CUSTOM KEY SET

Site Designed by Digital Canvas LLC
KA Industries, Inc.
155 Pierce Street, Unit 7
Somerset, NJ 08873
Toll-Free (800) 688-9202
Phone: (908) 226-7000
Fax: (908) 226-7007